Today we are proud to release our quarterly Hacked Website Report for 2016/Q3. This report is based on data collected and analyzed by the Sucuri Remediation Group (RG), which includes the Incident Response Team (IRT) and the Malware Research Team (MRT). The data presented is based on the analysis of over 8,000 infected websites.
This report compares data from our 2016/Q1 and 2016/Q2 reports. We enjoy sharing these insights with the hope that they will continue to help website owners strengthen their security posture.
CMS Analysis
Similar to what we saw in 2016 – Q1 / Q2, the three leading affected CMS platforms were WordPress (74%), Joomla! (17%), and Magento (6%).
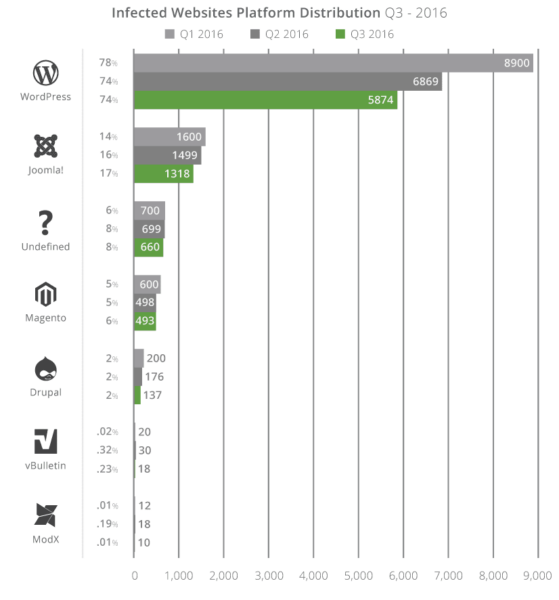
As we’ve mentioned before, this does not imply these platforms are more or less secure than others. Often the compromises analyzed had little, if anything, to do with the core of the CMS application itself, but more with improper deployment, configuration, and overall maintenance by the webmasters.h
Out-of-Date CMS at Point of Infection
In this section we assessed the percentage of CMS installations that were out-of-date at the point of infection. A CMS was considered out-of-date if it was not on the latest recommended security version or had not patched the environment with available security updates at the time Sucuri was engaged to perform incident response services.
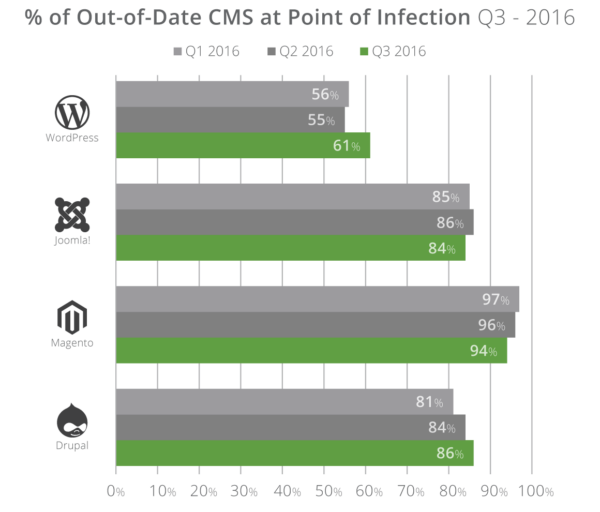
This quarter we noticed a 6% increase in out-of-date, vulnerable versions of WordPress installations at the point of infection. Drupal also experienced a 2% increase from Q2 to Q3. Similar to prior quarters, Magento (94%) and Joomla! (84%) websites were mostly out-of-date, and vulnerable, at the point of infection. Both Joomla! and Magento though saw a 1% and 2% decrease compared to prior quarters. We share these as general observations, they are not meant to dictate the state of a CMS being more or less secure than others as there are a number of contributing factors. Further details are explained in the report.
WordPress Analysis
The WordPress platform contributed to 74% of our sampling. With this in mind, we dive deeper into our data related to WordPress. Unfortunately, due to data corruption we were unable to include the plugin distribution, but hope to reintroduce it next quarter.
The top three WordPress plugins involved in website hacks continue to be TimThumb, Revslider, and Gravity Forms. This does not mean there are not others; it does mean that in the aggregate, no one plugin, beyond these three, has a footprint greater than 1% of the total infections.
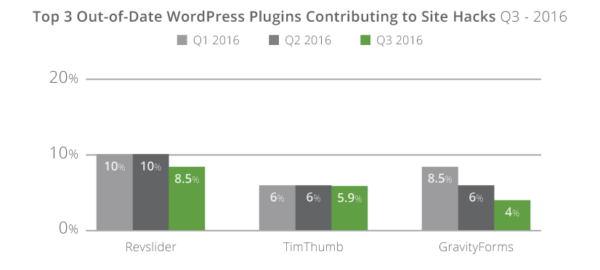
Although the top three plugins remained the same, we saw an improvement in Revslider, dropping 1.5% to 8.5%, and in GravityForms, dropping 2% to 4% (a total of 4.5% year to date). The total number of infected WordPress installations as a result of these three platforms has dropped significantly this year, from 25% in Q1 to 18% in Q3. The continued decrease is expected as more website owners and hosts continue to proactively patch out of date environments.
Perhaps the most disturbing dataset is the lack of change in TimThumb – likely due to the fact that many websites are still unaware that the script is on their site. In many ways, Revslider suffers from the same issue, where many website owners are unaware they have it installed as part of a theme. The TimThumb performance to date might be a roadmap of what we can expect from RevSlider in the coming years.
Blacklist Analysis
We continued our analysis of blacklists, which have the ability to adversely affect website owners. If you have been affected by a blacklist, learn how to remove a blacklist warning. Having a warning on your site by any one of the many authorities can adversely affect your brand and business economics.
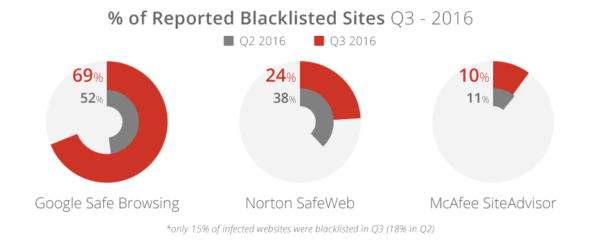
Approximately 15% of the infected websites were blacklisted (a 3% decrease from Q2). This indicates that approximately 85% of the thousands of infected websites we analyzed this quarter were freely distributing malware (without being blacklisted). These findings highlight the importance of continuous monitoring of your web property beyond traditional means like Google and Bing webmaster tools.
Malware Families
Understanding malware families is a crucial aspect of our research; it provides us the necessary insights to better understand the Tactics, Techniques and Procedures (TTP) cyber criminals are employing. Our research over the past quarter includes analyzing the various infection trends, specifically how they correlate to our malware families.
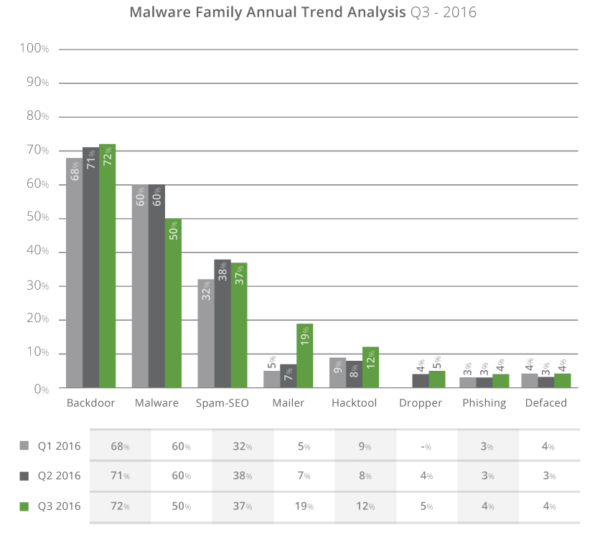
We found that 72% of all compromises had a PHP based backdoor hidden within the site this quarter and approximately 37% of all infection cases are misused for SEO spam campaigns (either through PHP, database injections or .htaccess redirects). We also saw a substantial increase in mailer scripts (12%) being employed as part of email Spam campaigns, and a 10% decrease in malware distribution.
Hacked Website Report – TL;DR
Here are a few highlights from the report:
- WordPress continues to lead the infected websites we worked on (at 74%).
- The top three plugins affecting WordPress continue to be Gravity Forms, TimThumb, and RevSlider.
- WordPress installations that were out of date at the point of infection increased from 55% in Q2 to 61% in Q3. Both Joomla! and Magento continue to lead the pack with out-of-date vulnerable installations at the point of infection.
- The blacklist telemetry showed a 3% reduction in sites being blacklisted, increasing the number of infected websites that are going undetected by blacklist engines to 85%.
- SEO spam continues to be an important issue at 37%. There was a sharp 12% increase in mailer scripts and a 10% decrease in malware distribution.
- A new dataset was introduced this quarter that depicted which files bad actors are modifying most consistently with each incident: index.php (25%), header.php (20%), and .htaccess (10%)
The report is available both on our site and in PDF format.
We truly hope that you find these insights valuable. We will continue to expand on the data we collect and report on, but as usual, if you have recommendations let us know.











